The 2022 Uber Breach
2022 has been a year of tech giants getting breached. Human fallibility continues to be, for the most part, the weakest link in company security. More on that later.
The latest victim is the ubiquitous ride-sharing company, Uber.
The 2022 Uber Breach - What, How, and Lessons Learned
This isn’t the first time Uber has been breached. In 2016 they allegedly paid hackers $100,000 to delete the data they stole and keep the breach a secret. A year and CEO change later, the hack was publicized, revealing that personal information from over 50 million Uber riders and the driver’s license numbers of 600,000 US drivers had been leaked.
Every publicized breach is a chance to learn and prepare. In this article, we will briefly cover what happened with the Uber breach of 2022 and then discuss what companies should do to shore up their defenses.
For more details about the breach itself, Uber maintains their own newsroom covering the situation.
Table of Contents
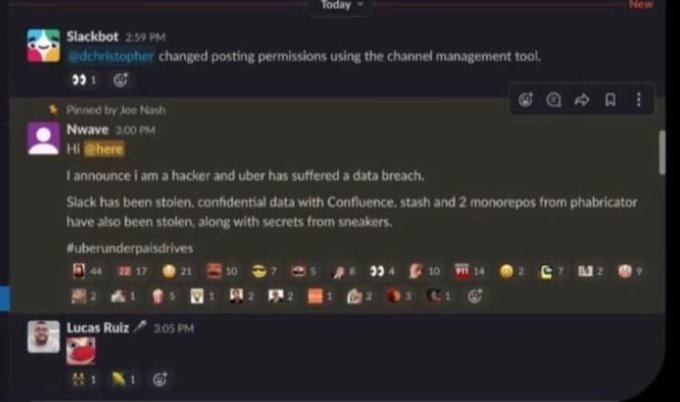
How did the Uber breach happen?
The 2022 Uber breach was a “social engineering” attack. In social engineering attacks, cybercriminals use psychology to manipulate users into disclosing secret information or taking an action that allows the criminal to access private data.
In this case, one Uber contractor unknowingly allowed the hackers the access they needed. Uber states that “It is likely that the attacker purchased the contractor’s Uber corporate password on the dark web, after the contractor’s personal device had been infected with malware, exposing those credentials.”
The attacker then employed an increasingly common attack called MFA (multi-factor authentication) Fatigue. They repeatedly attempted to log in with the stolen password, which caused the contractor to be spammed with authentication requests. Eventually, either by accident or to make it stop, the contractor accepted one such request.
With access to one account, the hacker was able to get into other employees’ accounts and further elevate their permissions. They took the opportunity to boast of their feat internally.
Uber has taken cautionary steps, including mandatory password resets and locking down its codebase.
Who was responsible for the Uber breach?
They believe LAPSUS$, a hacking group that has taken credit for breaches of Nvidia, Samsung, and Microsoft, to name a few, is responsible.
LAPSUS$ itself is an interesting rabbit hole. They first made headlines by hacking Brazil’s Ministry of Health and deleting the health records of millions of people (thankfully the government had backups). LAPSUS$ later breached Nvidia - a technology company famous for its GPUs - and demanded that they make their drivers open-source if they did not wish their data leaked. In March of this year, the London police arrested seven teenagers related to the group. All have since been released, and LAPSUS$ continues its prolific run.
LAPSUS$’s goal is unknown, nor do authorities know whether they have backing from a larger organization. Recent activity suggests that members operate from the UK and US, though some suspect ties to South America given their propensity for targeting that region.
For more information about LAPSUS$, Krebs has done great work documenting their activity.
What can we learn from the Uber breach?
The breaches at Microsoft, Cisco, Uber, etc. all have a common pattern. There were no incredible feats of “hacking,” where a genius criminal breaks through security systems with sweat dripping down their brow as shown on TV. Instead, the attacks were intentional, methodical, and exploited human fallibility.
Humans are the easiest and often the weakest target. Many people see through and avoid becoming victims of social engineering tactics. But among companies like Uber, which employs over 29,000 people and has 122 million users each month, or T-Mobile (victim of a major breach in 2021), which employs 75,000 people and outsources much of its customer support, there are more than a few prime targets for cybercriminals.
We may sound like a broken record exhorting you to educate your employees and demand security best practices. But seriously - educate your employees and demand security best practices!
If we’ve learned anything from recent breaches, it’s that they would not have been possible without successful social engineering.
How could the Uber breach have been prevented?
The Uber hackers followed two relatively simple steps:
- Buy compromised passwords
- Social Engineer an employee
Improve Password Hygiene
Individuals and companies can reduce the risk of compromised passwords by regularly scheduling password changes. Setting a reminder to appear every 90 days on your phone to change vital passwords and run manual security checks makes it less likely for your passwords to be available for purchase. There are also programs that will monitor personal devices in real-time. These precautions alone aren't enough, as even relatively new passwords can be compromised.
For added security and convenience, use a password manager like TeamPassword. Password managers encrypt and store all of your passwords in one secure location. Many even include built-in password generators and mandatory 2FA.
Use 2FA
To counter the second step - social engineer an employee - you should use the best 2FA available and stay calm in the face of urgent requests to bypass the security measures you have in place.
Not all 2FA methods are equally effective. Authenticator Apps that generate One-Time-Passwords (OTP) directly on your device and refresh them regularly are more secure than SMS sent via a cellular carrier to your phone. The danger of SMS is mostly due to the possibility of SIM-swapping, where a criminal convinces a carrier to transfer a customer’s number to the criminal’s own device, thus gaining control of any OTPs. The FCC is making attempts to stop this, but SMS is still widely used and remains vulnerable.
Using 2FA can be annoying. It requires you to use a second device, and the time it takes adds up. But the security it provides is worth the cost. So use it if you can.
Don’t Act - Ask
Finally, common sense and a healthy dose of skepticism are essential components of a strong defense. If a request for information seems urgent, doesn’t seem familiar, or make sense, then it’s best to pause, consider, and confirm. Call the sender or ask a colleague to take a look. No one wants to “cry wolf,” but cybersecurity is a complex subject, and caution will be appreciated more often than not.
It’s always better to get a second pair of eyes on the situation.
Consider Using Hard Tokens
The Uber breach has also raised questions about hard vs. soft tokens. Soft tokens are software-based like MFA that uses a passcode or pin. Hard tokens are physical objects that grant access, like a USB or fob.
Hardware tokens are generally much more secure, as proven by the failed phishing attack on Cloudflare and Google’s success in thwarting phishing. Someone has to physically steal the hard key to gain access. However, hard keys are more expensive to purchase and maintain, which has historically precluded them from all but the most high-security applications.
Final Thoughts
Cybersecurity is an incredibly dynamic field. Researching the Uber breach and LAPSUS$ motivated me to take inventory of my current 2FA settings and improve security where possible. Hopefully, this overview of the Uber breach has helped you identify an area of improvement for yourself and your company.